Summary of GNSS Vulnerabilities
Key Points:
1. GNSS spoofing attacks can be created relatively cheaply using:
- Software-defined radios ($150-300)
- Basic equipment like Raspberry Pi
- Even modified USB video dongles (FL2K dongles)
2. Anti-spoofing techniques discussed:
- Polarization-based detection looking at RHCP/LHCP signal characteristics
- Watermarking of GNSS signals (Chimera system)
- Multi-constellation use for increased resilience
- Monitoring tools and sensor fusion
3. Railroad Industry Case Study (BNSF):
- Uses GNSS for Positive Train Control (PTC) safety systems
- Challenges in urban/mountainous areas with limited satellite visibility
- Deploying 650 RTK reference stations across 28 states
- Currently limited by FCC to using only GPS and Galileo signals
- Testing various anti-spoofing/jamming solutions
4. Key Threats:
- Intentional jamming and spoofing
- Unintentional interference (e.g., from nearby electronics)
- Supply chain attacks
- Cyber attacks on receivers
5. Recommendations:
- Use multi-constellation receivers where possible
- Implement monitoring and detection systems
- Keep firmware updated
- Use dedicated RF channels for critical applications
- Consider encrypted RTK when available
The speakers emphasized that GNSS attacks are becoming more common and easier to execute, making robust detection and mitigation strategies increasingly important.
Military v. Civilian GNSS PNT Vulnerabilities and CM
In contrast, civilian users rely on unencrypted signals that are inherently more vulnerable to interference and manipulation. These commercial users cannot access military encrypted signals, with limited exceptions such as the Galileo Public Regulated Service (PRS) for critical infrastructure. Most civilian applications use simpler, lower-cost equipment due to commercial pressures and practical constraints. This combination of unencrypted signals and commercial-grade hardware makes civilian users particularly susceptible to interference, whether intentional or unintentional.
Both military and civilian users face common natural threats including solar storms, ionospheric disturbances, signal blockage from terrain or buildings, and multipath effects where signals reflect off surfaces. They also share vulnerability to unintentional interference from sources like RF emissions, poor installation practices, and system errors. Intentional threats affecting both groups include jamming, spoofing, and various forms of cyber attacks, though military systems typically have better inherent protection against these threats.
For civilian users, countermeasures must work within the constraints of commercial technology and unencrypted signals. Hardware solutions include multi-frequency receivers that can process signals on different bands, multi-constellation reception to use signals from multiple satellite systems, and improved antenna designs that balance performance with cost and size constraints. Software and signal processing techniques play a crucial role, implementing monitoring systems, interference detection, Receiver Autonomous Integrity Monitoring (RAIM), and multipath mitigation algorithms.
Civilian systems increasingly rely on system-level protections to compensate for their inherent vulnerabilities. These include backup positioning systems like eLoran or cellular networks, networks of reference stations to monitor signal quality, Real-Time Kinematic (RTK) corrections for improved accuracy, and integration with non-GNSS sensors. This systemic approach helps compensate for the lack of military-grade protection at the signal level.
The security gap between military and civilian GNSS capabilities presents a growing concern as society becomes more dependent on satellite navigation and timing. Critical civilian infrastructure, including financial systems, autonomous vehicles, and power grids, increasingly relies on vulnerable GNSS signals. This disparity is particularly worrying given the proliferation of low-cost jamming and spoofing devices, combined with readily available open-source software that can be used to mount attacks. The challenge moving forward will be developing cost-effective ways to protect civilian systems while maintaining their commercial viability and widespread accessibility.
Internet-exposed GNSS receivers pose threat globally in 2024 | Securelist
What is GNSS?
Global Navigation Satellite Systems (GNSS) are collections, or constellations of satellite positioning systems. There are several GNSSs launched by different countries currently in operation: GPS (US), GLONASS (Russia), Galileo (EU), BeiDou Navigation Satellite System (BDS, China), Navigation with Indian Constellation (NavIC, India) and Quazi-Zenith Satellite System (QZSS, Japan). These systems are used for positioning, navigation and timing (PNT) by a wide range of industries: agriculture, finance, transportation, mobile communications, banking and others.
There are three major segments involved in GNSS operations:
- The satellites themselves, orbiting Earth at an altitude of 19,000–36,000 kilometers (11,800–22,400 miles).
- The control segment consisting of ground-based master control stations, monitoring stations and data upload stations (or ground antennas). Monitor stations track satellites and collect various associated data, such as navigation signals, range or carrier measurements. They then transmit the data to the master control stations. The master control stations in their turn adjust the satellite orbit parameters if necessary, using data upload stations to upload commands to the satellites.
- Various user hardware, such as mobile phones, vehicles, etc. that receives satellite signals and uses them to derive position and time information to operate correctly.
Both monitor stations and user devices are equipped with GNSS receivers, the former being more complex than the latter. These receivers may be accessed through a control interface, which enables configuring and troubleshooting them. However, if accessed by an adversary, it may pose a significant threat given that critical operations, such as air traffic control and marine navigation, may rely on these receivers. In this article, we’ll review the state of GNSS receiver security in 2024.
What are the threats to GNSS systems?
There are several possible attack vectors against GNSS systems. First, satellite signal may be jammed. By the time a GNSS signal reaches a ground-based receiver, its power is rather low. If another device’s signal in the same or an adjacent frequency band is powerful enough, the receiver may not detect the GNSS signal. The interference may be both accidental and intentional. There’s a number of inexpensive devices available online and designed to jam GNSS signals.
Second, GNSS signal may be blocked in some areas by large structures, such as skyscrapers and other tall buildings. This could hardly be considered an intentional attack, however; as cities grow, the number of such areas may grow, too.
Third, GNSS signal may be spoofed. Unlike jamming, spoofing is always an intentional attack. The attacker uses a ground-based device, which imitates a satellite, providing invalid information to the GNSS receiver. As a result, the receiving device calculates an incorrect position.
Fourth, physical attacks against satellites are possible, although not likely. And, last but not least, a cyberattack can be conducted against a vulnerable GNSS receiver.
Internet-exposed GNSS receivers and attacks on them
In 2023, at least two black hat groups conducted multiple attacks against GNSS receivers. In May that year, SiegedSec, a hacktivist and crimeware group, gained access to satellite receivers in Colombia in response to a hacker being arrested by authorities. In mid-2023, the group targeted devices belonging to multiple entities in the U.S., and claimed to have accessed satellite receivers in Romania. Although they haven’t caused any damage apart from accessing sensitive data and publishing screenshots through their channels, unauthorized access by an attacker to GNSS receivers can be a lot more destructive.
Another group attacking satellite receivers in 2023 was GhostSec. Throughout the year, they targeted numerous GNSS receivers in various countries including Russia and Israel. In some of the attacks they claimed to have not only accessed but also wiped data from the compromised satellite receivers, which illustrates the possible damage from such incidents.
Cybersecurity firm Cyble analyzed the attack surface against satellite receivers from five major vendors, and found out that as of March 2023, thousands of these receivers were exposed online. Broken down by vendor, the numbers were as follows:
| Vendor | Number of exposed receivers | Top countries |
| GNSS-1 | 3,641 | USA Japan Canada |
| GNSS-2 | 4,864 | Australia Greece Italy |
| GNSS-3 | 899 | Russia Poland USA |
| GNSS-4 | 343 | South Korea USA France |
| GNSS-5 | 28 | China Thailand USA |
Internet-exposed GNSS receivers in 2024
A year later, we decided to look at how the situation had changed. During our research, we analyzed information on satellite receiver vulnerabilities that had already been available online. Kaspersky solutions were not used to gather the information on these vulnerabilities; instead, third-party search engines designed to map and gather information about internet-connected devices and systems were used.
We first performed research similar to that done by Cyble (as far as we could guess their methodology) by searching for all exposed instances produced by five major GNSS receiver vendors without specifying that they should be satellite receivers. Our investigation revealed that, as of July 2024, 10,128 instances used globally were exposed over the internet, which was even more than in March 2023.
| Vendor | Number of exposed receivers | Top countries |
| GNSS-1 | 5,858 | USA Ecuador Jamaica |
| GNSS-2 | 2,094 | Australia Thailand Russia |
| GNSS-3 | 901 | USA Germany Russia |
| GNSS-4 | 890 | Austria USA France |
| GNSS-5 | 385 | Thailand USA China |
With these results, we conducted broader research covering 70 GNSS receiver vendors used globally. This time, we performed a more specific search for exposed instances that included the vendor name and the use of “GNSS” systems clearly specified.
Our research revealed that 3,028 receivers remained vulnerable to attacks over the internet.
TOP 5 vendors whose GNSS receivers are vulnerable to internet attacks (download)
We used the information collected above to compile a list of countries with the highest numbers of mentions among those most affected by the exposed instances for the major GNSS receiver vendors. Most vulnerable receivers by a specific vendor were largely found in the United States, Germany, Australia, Russia and Japan.
TOP 5 countries with the highest numbers of exposed receivers by certain vendors (download)
In a July 2024 global overview not limited to specific vendors, we found almost 3,937 GNSS instances accessible over the internet. From the geographical point of view, most of the exposed receivers – over 700 instances – were located in Ecuador. Jamaica was the second with 500 instances, closely followed by the United States. Almost 400 exposed receivers were found in the Czech Republic and China, and almost 300 were located in Brazil. Japan, Russia, Canada and Germany were among most vulnerable countries, too.
TOP 10 countries with the highest numbers of exposed receivers (download)
If we look at the anonymized data about the entities that use these exposed instances, we can see that most of the vulnerable receivers belong to organizations in the following industries: telecommunications, cloud computing and energy. However, at least one e-commerce retailer is also using exposed GNSS receivers.
TOP 10 companies that use exposed GNSS receivers (download)
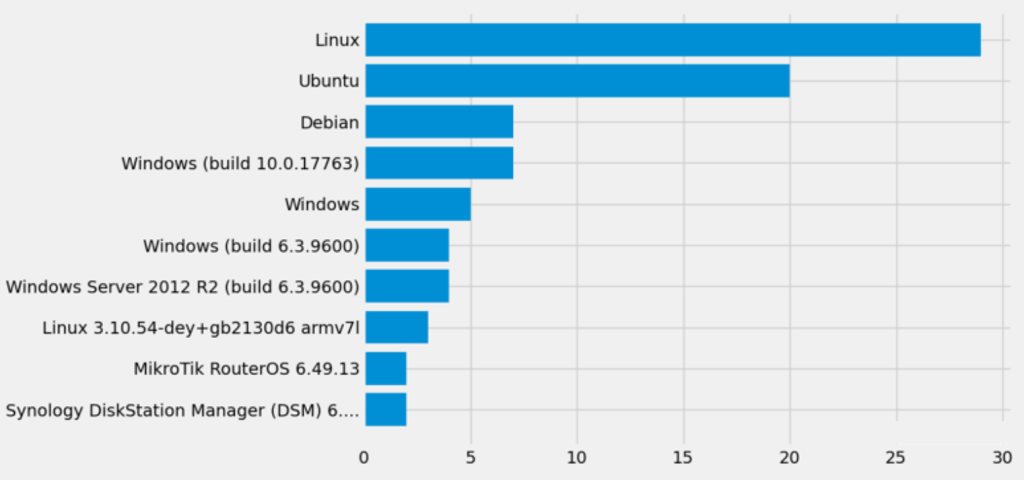
Most of the discovered instances ran on various open-source and proprietary Linux distributions. However, we also found exposed Windows-based receivers. Moreover, different devices had different versions of the OS installed, which made the attack surface on the vulnerable GNSS receivers even broader.
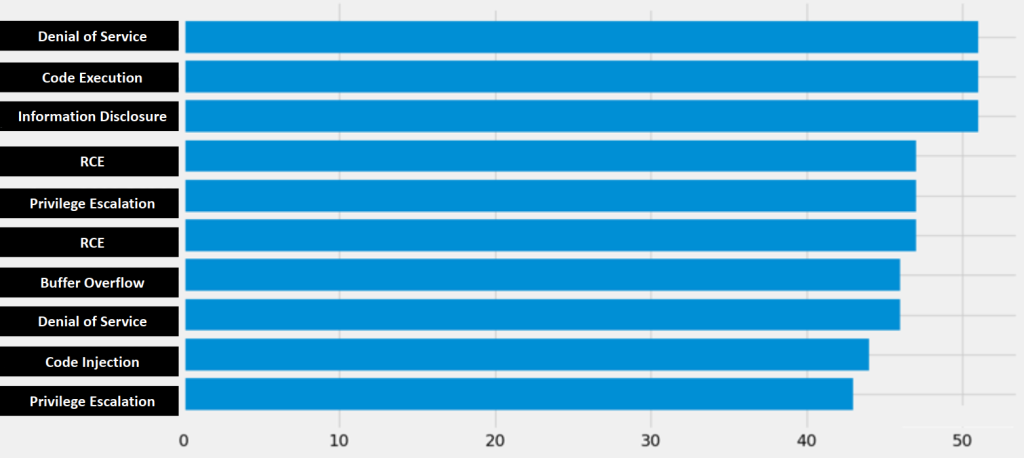
The exposed devices were vulnerable to a range of flaws, which could cause various types of damage to the system. Among the most frequently occurring vulnerabilities in the GNSS receivers were denial of service vulnerabilities, which could render the device useless if exploited; exposure of information resulting in data breaches, privilege escalation flaws, a buffer overflow, and several code injection or execution flaws that could result in the attacker gaining control over the receiver.
In November, we performed the global research again to find out that the number of exposed receivers reached 4,183. Compared to July, there was a slight shift in the geography of these receivers: while Ecuador remained the number 1 affected country, Jamaica, Czech Republic and Russia left the TOP 10, Germany jumped to the second place, and Iran entered the list as the fourth most vulnerable country.
TOP 10 countries with the highest number of exposed receivers, November 2024 (download)
Besides basic cybersecurity rules that equally apply to all computer systems, there are specialized tools that are designed to address space-related threats. For example, to improve threat identification and information exchange in this area, the Aerospace Corporation has created the Space Attack Research and Tactic Analysis (SPARTA) matrix, designed to formalize TTPs of space-related threat actors.
The SPARTA project also provides a mapping of MITRE’s D3FEND matrix, which covers possible countermeasures and defense tactics, to space-related threats. This mapping can help organizations develop a robust defense for their space systems.
Conclusions
GNSS systems are vital for a wide range of industries that rely on satellites for positioning and time synchronization. An attack against such a system may cause significant damage to the target organization. There are several ways an attacker can interfere with a GNSS. Some of these, such as physical attacks on satellites, are rather expensive and unlikely, while others are easy enough for a malicious group to pull off. One of these vectors is exploitation of ground-based GNSS receivers, which are available over the internet and vulnerable to known or as-yet-unknown flaws. The year 2023 saw a series of attacks on GNSS receivers by hacktivist groups.
As the results of our research show, as at July 2024, there were still nearly 4000 vulnerable devices that could be exploited by adversaries. To protect their systems from internet-based attacks, organizations should keep GNSS receivers unreachable from the outside. If internet access is a necessity, we recommend protecting your devices with robust authentication mechanisms.


No comments:
Post a Comment